In brief: Apple and CEO Tim Cook will likely be feeling quite smug following a report that Israeli company Cellebrite's widely used phone-unlocking tools are ineffective against up-to-date iPhones. On the other hand, Cellebrite's kit can break into the majority of Android phones.
Cellebrite's Universal Forensic Extraction Device (UFED) is widely used by law enforcement agencies to unlock phones and extract their data. A recent report claims the company's technology helped unlock the phone of Thomas Matthew Crooks, the man who almost assassinated Donald Trump, just two days after the shooting. It was never revealed what model of phone Crooks had.
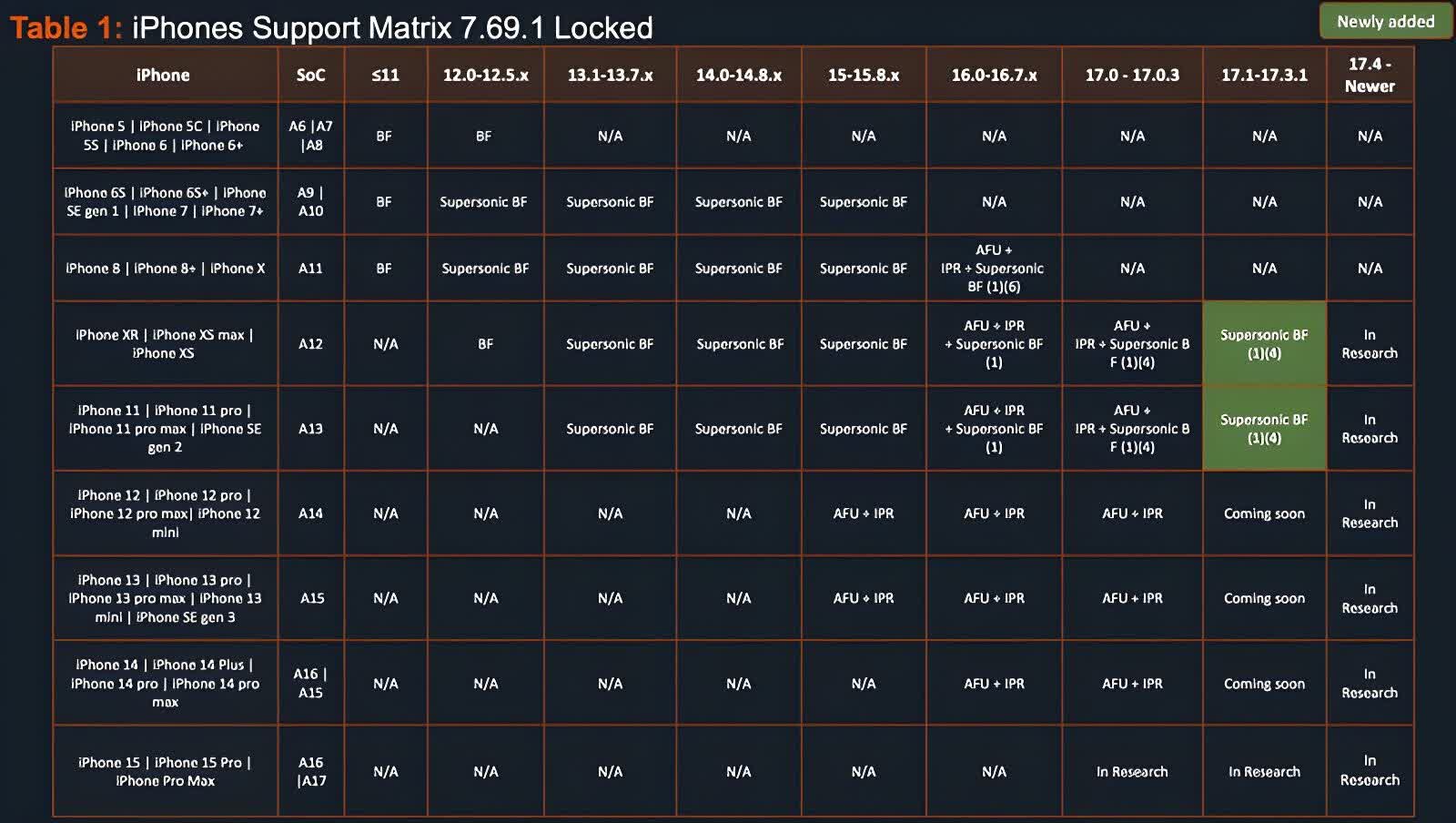
The Cellebrite iOS Support Matrix, obtained by 404 Media, reveals that the company still has not managed to break into iPhones running iOS 17.4 (launched on March 5) or later – the document lists them as still being "in research."
The document also reveals Cellebrite cannot break into most iPhones running iOS 17.1 to 17.3.1. However, the company recently added support for the iPhone XR and iPhone 11 lines running these iOS versions as hardware vulnerabilities in the handsets make them exceptions. The table lists the status of iPhone 12 and newer models running iOS 17.1 to 17.3.1 as "coming soon," suggesting support is on the way.
MacRumors reports that Apple's own data from June showed 77% of all iPhones and 87% of iPhones introduced in the last four years are running a version of iOS 17.
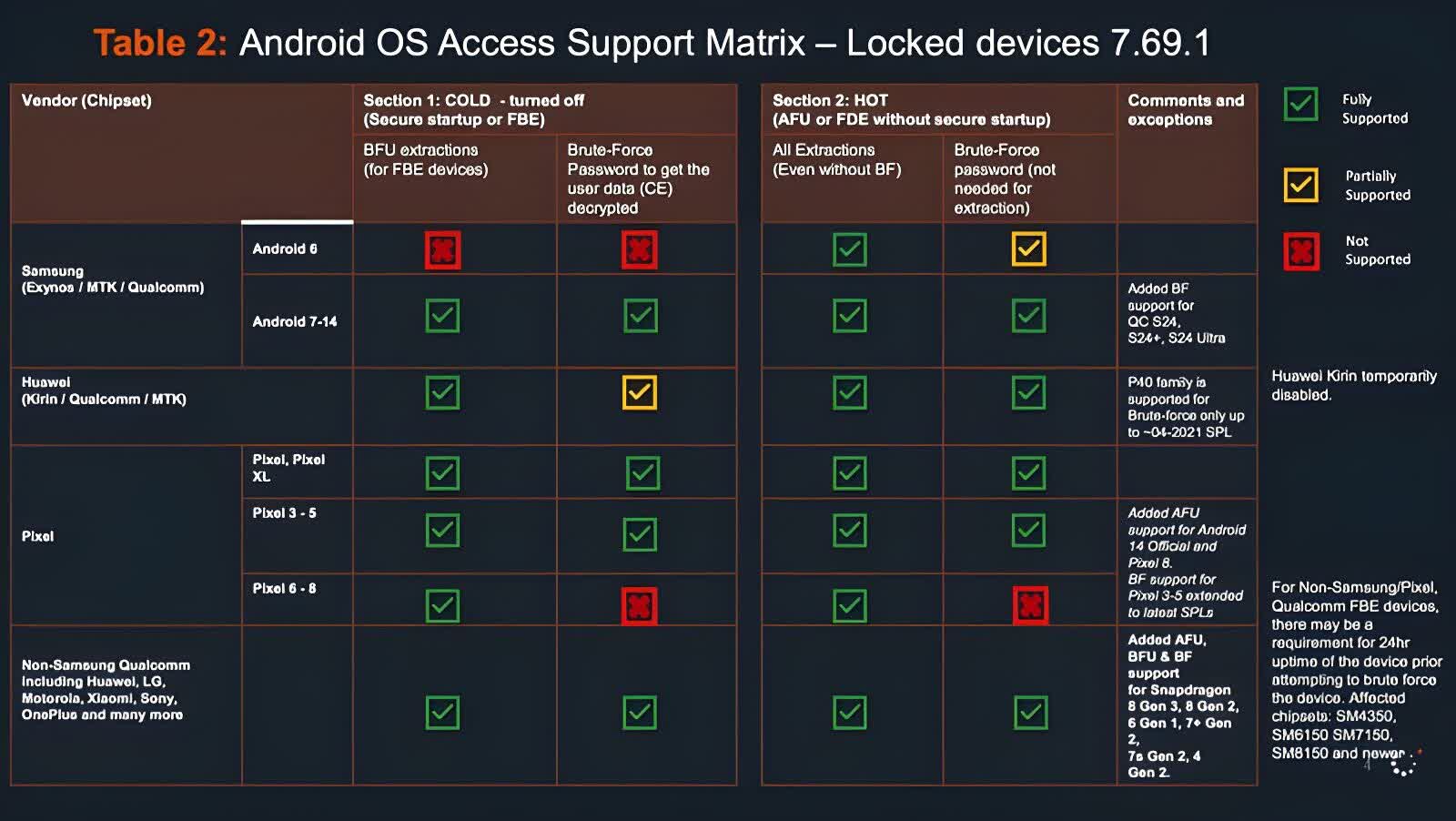
Most Android devices are vulnerable to Cellebrite's tools, but there are some exceptions, including the Google Pixel 6, 7, and 8, which cannot be broken into if obtained while powered off – the cold-boot process blocks the exploit used.
Samsung phones running Android 6 are also safe if they are turned off when obtained, but those running Android 7 to 14 are fully supported. Other phones running Android 7 to 14 can also be compromised by Cellebrite's brute force attack.
Cellebrite relies on identifying vulnerabilities in iOS and Android that allow its tools to crack locked devices. One method it uses is overriding systems that limit the number of passcode attempts on a device.