In brief: Bad actors continue to devise new ways to make staying safe online more challenging. The latest method is particularly innovative, as it bypasses the built-in security protections of iOS and Android by using Progressive Web Apps. These PWAs mimic legitimate apps on your phone, tricking users into handing over bank credentials and other sensitive data.
Installing apps from unofficial channels on both iOS and Android is now more difficult than ever. While iOS outright forbids it, Android is more lenient, allowing you to "sideload" apps from other sources if you choose. However, the process isn't straightforward – you need to check a couple of boxes in prompts that warn you about the risks involved.
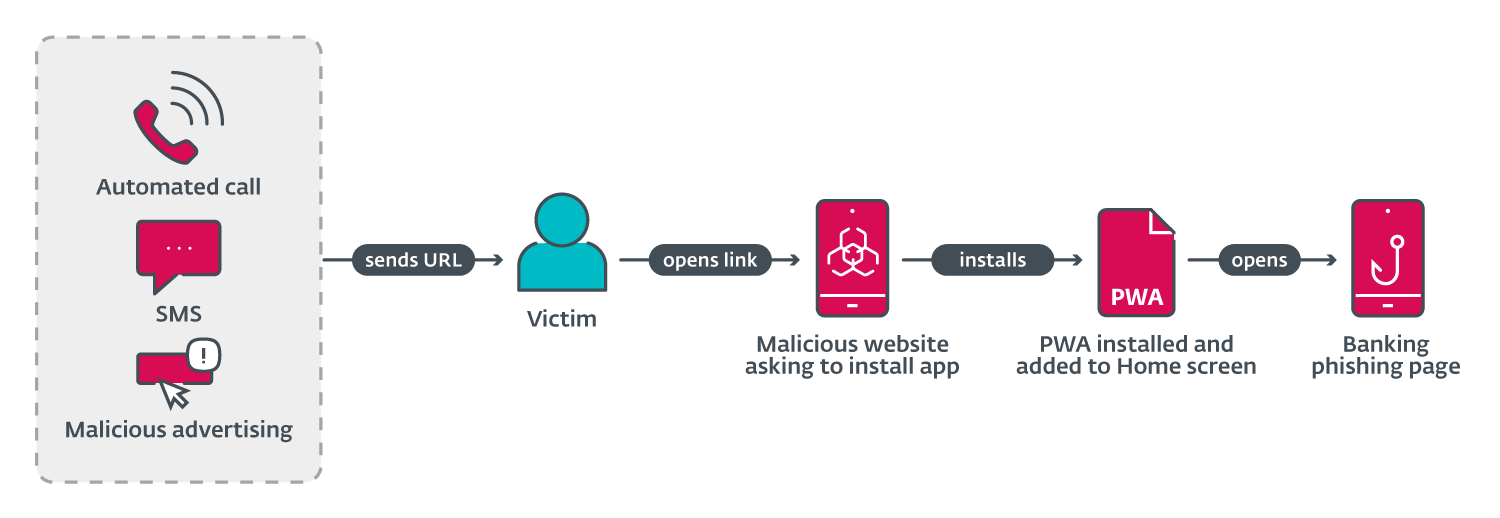
Unauthorized app installations are no easy feat for hackers either. So, clever phishers have devised a sneaky workaround. Security firm ESET has highlighted how bad actors are using a special type of app called a Progressive Web App to bypass security measures. PWAs run entirely in your browser using web standards, with no native code required. You might have encountered them when a website or browser prompts you to install a site as an app.
Here's how the attack unfolds: you receive a sketchy text or see an ad on Facebook or Instagram with a link. If you click it or any attached links, it launches a page mimicking the legitimate app store for your platform. Then, it prompts you to install an "update" for your bank's mobile app.
For Android users, clicking the install button triggers a WebAPK installation – bypassing any warnings about unknown apps due to some Chrome functionality that the phishers are exploiting. On iOS, you get an animated popup styled just like Apple's system prompts, instructing you on how to add the PWA to your home screen.
Once the phishing PWA is installed and added to your home screen, looking completely legitimate, it prompts you to enter your online banking credentials to access your account via this new "mobile banking app." In reality, it's just relaying that sensitive information directly to the scammers' servers.
A savvy user might be able to distinguish a PWA from a regular app and realize that apps can't be installed directly from a web browser. But for the average person, it's easy to fall for the ruse.
ESET's researchers have observed this tactic being used to target bank customers primarily in Czechia, with some victims in Hungary and Georgia as well. While the company has successfully negotiated the takedown of multiple phishing domains involved in this scam, it remains unclear what actions Apple and Google will take to address the issue.