Why it matters: A zero-day vulnerability that affects ISPs and MSPs is a serious concern, as it could easily impact critical infrastructure and national security if exploited on a larger scale. Moreover, the suspected involvement of Chinese state-sponsored hacker groups like Volt Typhoon and Bronze Silhouette make the vulnerability particularly alarming. The risk of widespread disruption underscores how susceptible our essential services are to cyberattacks.
Black Lotus Labs has discovered a zero-day vulnerability in Versa Director servers, a virtualization platform widely used by ISPs and managed service providers. This vulnerability, potentially linked to Chinese state-sponsored hacker groups, poses a significant risk to these organizations.
Identified as CVE-2024-39717, this critical flaw was publicly announced on August 22, 2024, and affects all versions of Versa Director software prior to version 22.1.4. The vulnerability is particularly concerning for ISPs and MSPs, as they depend on Versa's software-defined wide area network (SD-WAN) applications to manage network configurations.
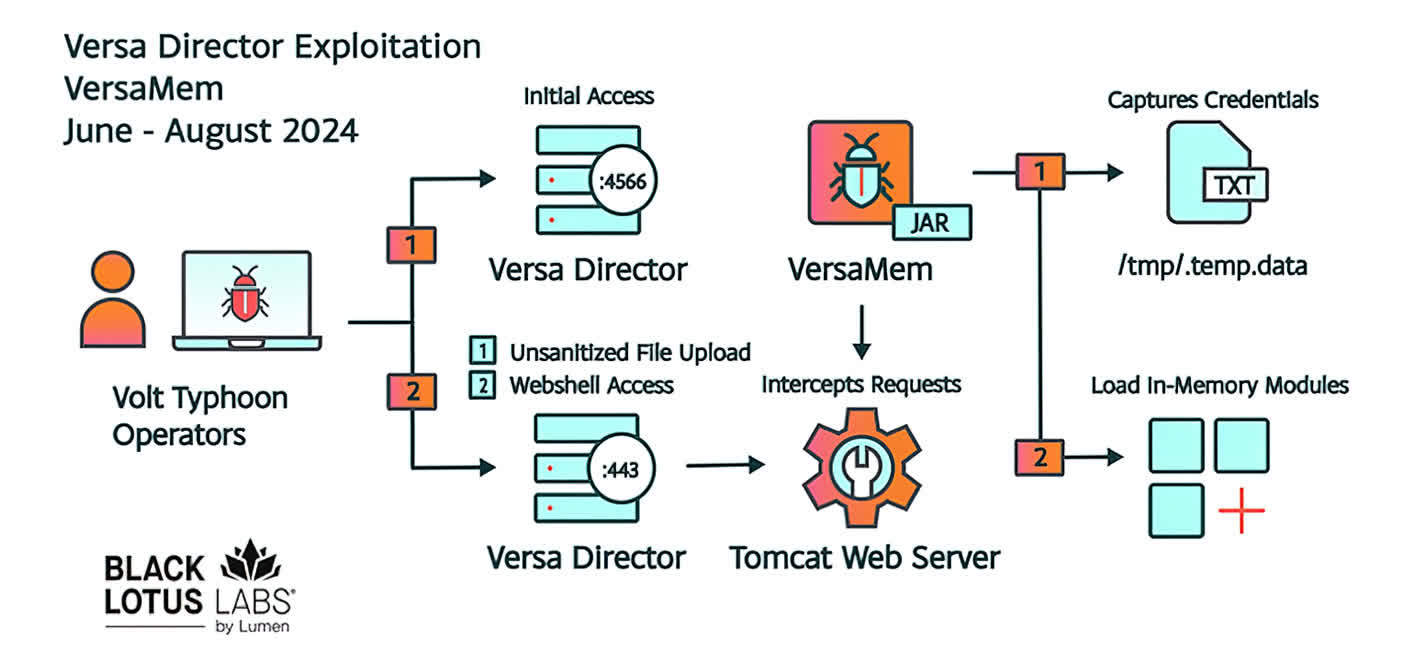
The vulnerability's discovery has caused alarm due to its potential to penetrate enterprise networks via Versa Director servers, which are responsible for essential network functions. Black Lotus Labs identified a custom web shell, named "VersaMem," that exploits this flaw to extract login credentials.
A notable feature of VersaMem is its modularity, which allows it to load additional Java code directly into the server's memory, effectively evading detection.
Global monitoring data from Black Lotus Labs reveals that the vulnerability has been exploited through compromised small-office/home-office devices in attacks targeting four victims in the United States and one abroad. These attacks, primarily affecting the ISP, MSP, and IT sectors, have been ongoing since June 12, 2024.
The attackers initially gain access by exploiting an exposed management port on the Versa Director, designed for connecting Director nodes for high availability, which they then use to deploy the VersaMem web shell.
Black Lotus Labs suspects that Chinese state-sponsored hacker groups, known as Volt Typhoon and Bronze Silhouette, are orchestrating the exploitation of this vulnerability. Their analysis indicates that Volt Typhoon is actively targeting unpatched Versa Director systems.
The exploitation campaign is considered highly significant by Black Lotus Labs due to the severity of the vulnerability, the sophistication of the threat actors, and the critical role of Versa Director servers in network operations.
Organizations using Versa Director are strongly advised to upgrade to version 22.1.4 or later. Additionally, they should review security advisories issued by Versa Networks on July 26, 2024, and August 8, 2024.
The severity of this vulnerability and the potential consequences of compromised Versa Director systems led Black Lotus Labs to publicly release this information.
Lumen Technologies has also shared this critical threat intelligence with relevant US government agencies to alert them to the potential risks to national strategic assets.