Another ransomware attack is spreading across Russia and Ukraine today. According to Reuters, the large-scale attack was launched earlier today and has already affected several systems. In Russia, oil company Rosneft and several banks have been affected. Ukraine's international airport has compromised systems, as does A.P. Moller-Maersk, a Ukraine-based shipping company.
The attackers want $300 in Bitcoin to return computers to operating conditions. Maersk, which also has offices in the Netherlands, says their computers in Rotterdam have been affected as well. The company says the attack has shut down its systems in several regions, and it knows that the attacks are related because the ransom messages are the same.
The message reads, "If you see this text, then your files are no longer accessible, because they have been encrypted. Perhaps you are busy looking for a way to recover your files, but don't waste your time. Nobody can recover your files without our decryption service."
Several other companies in Russia and Europe are reporting cyber attacks as well, but it is unknown if they are being affected by the same malware. While the attacks appeared to be similar to last month's WannaCry outbreak, security experts had first identified the malware to be Petya. But later on rectified, and Kaspersky is calling it 'NotPetya'.
The ransomware encrypts a computer's hard drive and only provides the decryption key upon payment.
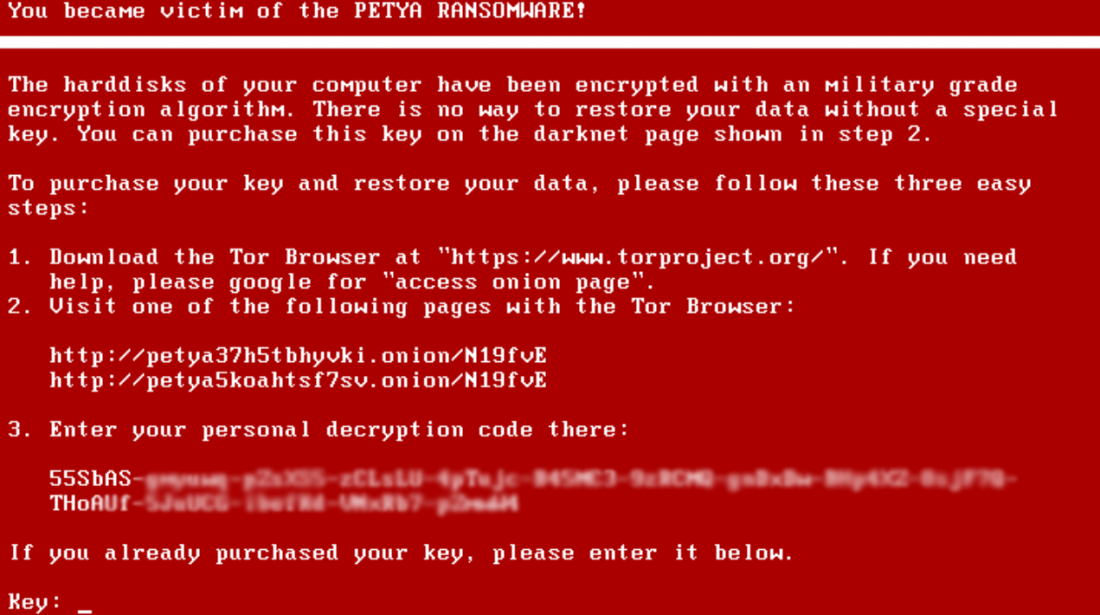
Petya is not new. We reported on how to get your files back from the malware last December. This is believed to be a variant of the software. The malware's vector seems to be the typical phishing email scheme. So as always be vigilant about any emails that you were not expecting.
The latest from @kaspersky researchers on #Petya: it's actually #NotPetya pic.twitter.com/uTVBUul8Yt
--- Kaspersky Lab (@kaspersky) June 27, 2017
Russia and Ukraine are the most affected countries thus far, but attacks have now been recorded in Poland, Italy, the UK, Germany, France, and the US. "We can confirm that a modified EternalBlue is used for propagation at least within the corporate network," researchers said. They also urge companies to be sure their computers and servers are updated to limit risk.
