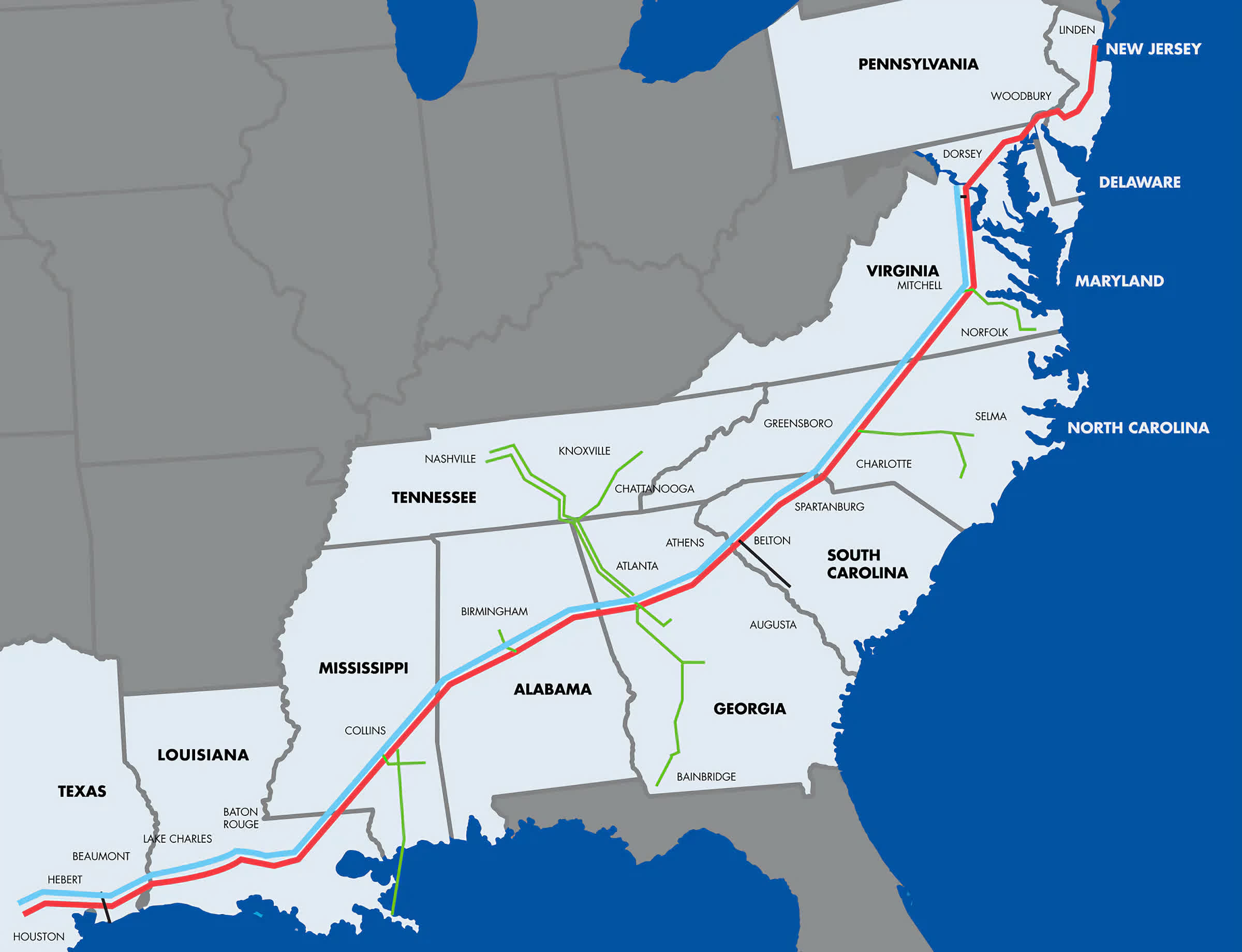
A hot potato: The 5,500-mile Colonial Pipeline has been offline for the last four days, after a ransomware attack compromised its computer network. DarkSide, an Eastern European group of cybercriminals believed to be the authors of the attack, posted a statement on the dark web noting that its sole goal is money, with no connection to geopolitical interests and no intention of "creating problems for society."
Recently, the main fuel supply line serving the US East Coast was shut down after its operator suffered a security breach in its digital infrastructure. The Colonial Pipeline stretches for over 5,500 miles to provide around 45 percent of the fuel needs of the region, which makes this potentially the largest successful cyberattack on US infrastructure to date.
The company says it shut down the main part of the pipeline as a precaution, while it only brought "smaller lateral lines between terminals and delivery points" back up. A third party security firm was hired to investigate the incident, and preliminary findings point out to ransomware attack that affected Colonial's business computer systems. The attackers have encrypted almost 100 gigabytes of data from the Georgia-based company and are threatening to release it to the public if it doesn't pay the ransom.
Today, the FBI confirmed suspicions that a group of Eastern European cybercriminals calling itself DarkSide is behind the attack, noting "we continue to work with the company and our government partners on the investigation." At the same time, the hacker group posted a statement on the dark web explaining that its one and only goal is to make money, and that it's not tied to a "defined" government or political entity.

Interestingly, the group also explained that it has no intention of "creating problems for society," which is an understatement of the ruckus created through the disruption of almost half the supply of gasoline and diesel fuel to the US East Coast.
And while it wouldn't say how much it demanded in ransom money from Colonial, it did claim that it has breached more than 80 companies since August 2020, after previously extracting millions from individuals.
The most peculiar part of DarkSide's statement is where the group promises to introduce a moderation process into its workflow in order to "avoid social consequences in the future."
Boston-based security firm Cybereason told CNBC that DarkSide is a "ransomware as a service" provider that tries to project the image of being ethical, with clear rules of conduct that are against attacking medical and educational institutions, government agencies, and even non-profit organizations – especially if they're located in former member countries of the Soviet bloc. The group even claims to donate portion of its profits to charity.
Colonial doesn't say if it will pay the ransom, but the company is optimistic about its goal to "substantially restore operational service by the end of the week." The Biden administration has issued an emergency declaration in 17 states and Washington DC in an effort to keep deliveries going and help Colonial return to normal operations as soon as possible.
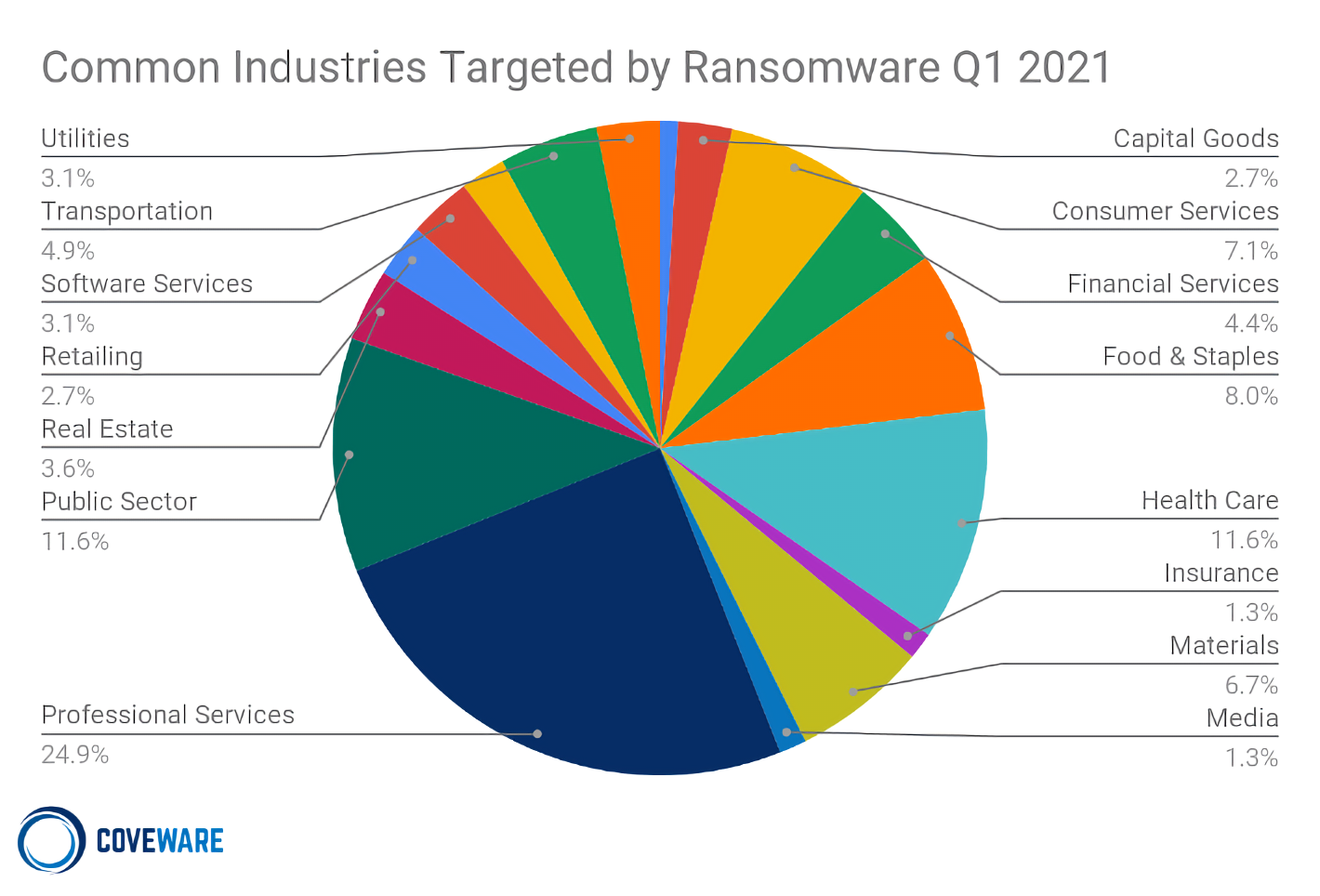
In other news, Axa SA, one of the biggest insurance companies in Europe, announced that it will stop offering policies that cover ransomware payments in France, which could encourage more insurance companies to follow suit.
This probably shouldn't surprise anyone, considering the recent surge in ransomware attacks on companies big and small, including computer manufacturer Acer and game publisher CD Projekt Red. It's estimated that in 2020, over 41 percent of cyber insurance claims came from ransomware, with damages totaling more than $20 billion, almost double the amount estimated for 2019.
The number of ransomware attacks has increased by an order of magnitude in the last twelve months, but at least there's been a decrease in ransomware payments as more victims refuse to pay. Today's news is, perhaps, the best reminder to always create multiple backups of your important files and exercise maximum caution when receiving suspicious emails or invitation links on messaging platforms.